The September Windows 11 update add protections against malicious applications and drivers, phishing, credential misuse, and more.
Windows 11 2022 (22H2 release) is now out, and Microsoft has once again placed a heavy emphasis on security. The good news for this release is that even Windows Home versions can receive some of the key security features with no additional Windows or Microsoft 365 licensing. Review the Windows 11 22H2 security baseline documents and begin to test these features.
Windows 11 release cadence
First, a reminder: With Windows 11 feature releases now only come out once a year. Major security changes occurred in the first release of Windows 11 (21H2) as well as this release of 22H2. Between each major feature release will be small incremental changes called “moment” releases. For example, expected future moment updates will be features such as tabs and a new sidebar to File Explorer.
In addition, in certain Microsoft applications, “suggested actions” will prompt users about the next steps to take in applications like Microsoft Teams. These moment releases or “controlled feature rollouts” will be off by default in business releases but will be included in preview releases. Group policies to better control these incremental changes will be available so that you will be able to deploy those changes in your network as you see fit.
Windows 11 Smart App Control
First up is a new feature called Smart App Control. If you remember, the Windows 10 S mode allowed you to install applications only from the Microsoft Store where they had been vetted. Smart App Control is similar in goal but totally different in implementation.
This time Microsoft has a cloud-based directory of trusted applications that it has vetted and has stored the hash values. If Smart App Control is enabled on a newly deployed Windows 11 22H2, any installed binary will be vetted. If the application is not on the list, then the digital signature of the application will be inspected. If it has a valid digital signature, the application will be allowed to be installed. If you have a line-of-business application that does not sign its code, reach out to the vendor to ensure that it is code-signed. This should be a standard process for any good vendor practices.
Smart App Control cannot be enabled after you have installed the operating system. If you have already deployed Windows 11 22H1, you must reinstall 22H2 from scratch to use this feature. Furthermore, if you later disable the setting to get around a needed application that isn’t on the approved list, you won’t be able to undo this choice; it’s a one-way deployment. For these reasons, firms may want to tackle the untrusted application problem with a different tool. You can use Microsoft Intune with Windows Defender Application control to apply policies to control what is installed.
Smart App Control is built on the same OS core capabilities used in Windows Defender Application Control. Smart App Control is provided on all Windows client editions with clean installations of Windows 11 2022 Update.
Alternatively, enterprise IT teams can use Microsoft Intune with Windows Defender Application Control (WDAC) to remotely apply policies to control what apps run on workplace devices. The licensing requirements for this are interesting: “Enterprises can enforce WDAC policies on any edition of Windows 10 and Windows Server 2016 without additional licensing; the creation of policies requires Windows 10 Enterprise.” To use Windows 11 in the first place, you’ll need the necessary hardware for Windows 11 including a Trusted Platform Module (TPM) as well as the proper virtualization hardware.
Microsoft Vulnerable Driver Blocklist
Malicious drivers are a large problem and Windows 11 22H2 is upping the ante on protecting the operating system. Hypervisor-Protected Code Integrity (HVCI) and blocking known vulnerable drivers via the Microsoft vulnerable driver block list are two processes that now protect Windows 11. Since Windows has strict requirements for code running in the kernel, cybercriminals commonly exploit vulnerabilities in kernel drivers to get access.
Kernel Mode Hardware Enforced Stack Protection is hardware specific and has a dependency that requires Intel Tiger Lake processors and beyond or AMD Zen3 and beyond. This setting has a dependency on HVCI (Virtualization-Based Protection of Code Integrity). If you do not have these hardware features, you will not see this offered to you.
Enhanced Phishing Protection
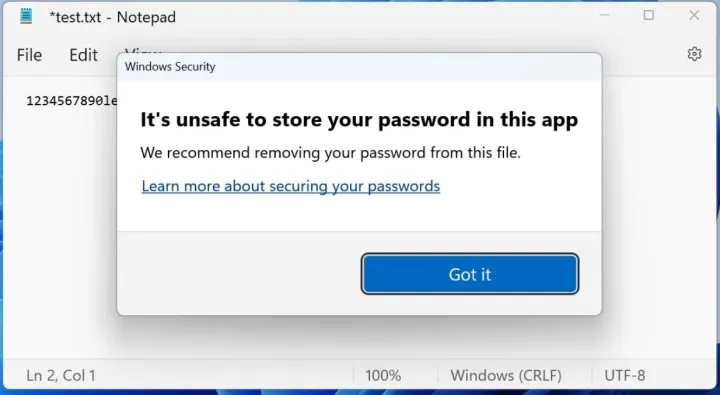
Enhanced Phishing Protection is included in 22H2 by default in all versions of Windows 11 22H2. While you do not need Microsoft 365 Defender to enable this feature, that license gives you additional logging and reporting. It’s based on the Microsoft Defender SmartScreen infrastructure to alert the end users that websites or applications are attempting to steal credentials. With an appropriate Microsoft 365 license, it can also warn users if they re-use a corporate credential in another application or web site. If a user saves a password in Notepad, Wordpad, or another Office application, if you have licensing for Microsoft Defender for Endpoint (E5 or Microsoft business premium, or standalone license), it will be flagged and logged.
Printer protection
Nearly every month some sort of print spooler patch must be applied to our network computers. Windows 11 22H2 introduces additional settings as well as builds on fixes that have been introduced to harden print features. For example, the ability to manage processing of queue-specific files (CopyFilesPolicy) was first introduced as a registry key in response to a Windows Print Spooler remote code execution vulnerability (CVE-2021-36958) in September 2021. This setting allows standard color profile processing using the inbox mscms.dll executable and nothing else. The security baseline now is to configure this setting to “Enabled” with the option of “Limit queue-specific files to color profiles”..
Allow administrator account lockout
Every release of Windows 11 adds and tweaks group policies. Windows 11 22H2 adds a group policy to assist in remote desktop attacks that are often entry points for ransomware. This policy located under “Security Settings”\”Account Policies”\”Account Lockout Policy” has been added to mitigate brute-force authentication attacks.
Credential protection
Windows 11 22H2 supports additional protection for the Local Security Authority (LSA) to prevent code injection that could compromise credentials. The new Local Authority Subsystem Service (LSASS) protects enterprise joined Windows 11 devices and ensures that Microsoft will only load trusted, signed code.
Domain join or Microsoft account mandate
Windows 11 22H2 is best when it’s combined with Microsoft 365 and an appropriate license that includes additional security features. For large enterprises this would be a Windows 11 Enterprise E5 or Microsoft 365 E5 license. Small businesses under 300 seats can purchase a subscription to Microsoft 365 Business Premium and get many of the features of the E5 suite at a lesser cost.
While it’s strongly encouraged even in Windows 11 professional version to join with an Azure AD account or Microsoft account, you can still join a local domain or even deploy a local account with a minimum of issues. However, joining the platform to Azure AD will provide you with the best security options and blend of cloud protection and hybrid options.
More WIndows 11 protections in store
Microsoft has already begun testing new features to make the operating system even more secure. In the Insider release preview build 25206, the SMB server service now defaults to a two-second default between each failed inbound NTLM authentication. If an attacker is using brute-force techniques to guess the password from a database, it will slow down that attacker so the technique will take a drastically longer period of time.
Zero trust
Many of us are attempting to do a better job of deploying machines with stronger credentials, better password protection and lesser administrative rights. Regardless, if you deploy with zero trust in mind or merely ensure that your credentials are better protected, Windows 11 22H2 provides more tools needed to keep one step ahead of the attackers.
Windows 11 22H2 won’t be the last of Microsoft’s pushes for more security for our networks. While many of us will have to wait to see these Windows 11 hardware mandates in our networks, they showcase that security isn’t just important to the software. The computer hardware must do its part as well to ensure that we keep our networks protected. Take the time now to test, review and deploy 22H2 and take advantage of these security features.